Advanced persistent threat (APT)
APT usually refers to a group, such as a foreign government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack.
Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target.
http://en.wikipedia.org/wiki/Advanced_persistent_threat
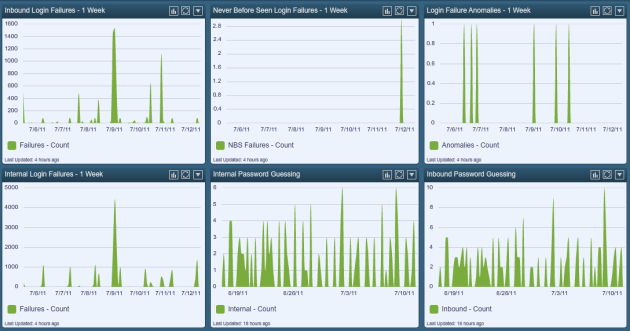
13 Signs that bad guys are using DNS Exfiltration to steal your data
UDP 53 Indicators of Exfiltration
- encrypted payloads
- MD5, SHA1, SHA256 hashed subdomains
- lots of requests to restricted or suspicious domains
- lots of requests to one domain
- lots of requests to fast flux domains
- plain text requests of subdomains
- DNS replies have private addresses
- DNS replies have single IP address
- lots of DNS traffic going to bad guy country
- DNS replies have patterned encoding
- Packet size outside the normal distribution
- Pattern of many requests to specific domains in round robin pattern
- Spike in DNS byte count across normal traffic patterns
- Multiple Pointer Records for single query
- PTR records do not appear to be coming from org ASN
http://theworldsoldestintern.wordpress.com/2012/11/30/dns-exfiltration-udp-53-indicators-of-exfiltration-udp53ioe/
http://code.google.com/p/dnscapy/
https://github.com/bigsnarfdude/DFTP
http://blog.strategiccyber.com/2012/12/19/hacking-like-apt/
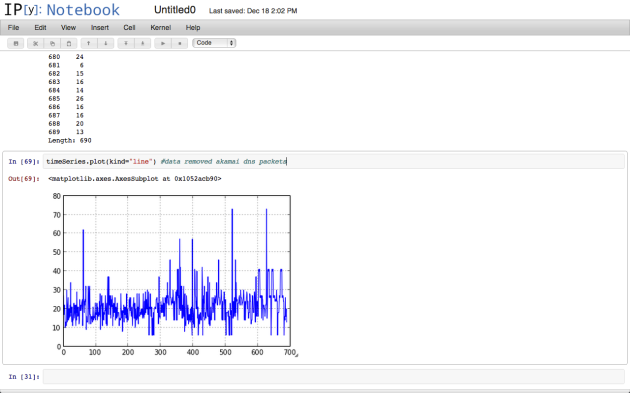
https://bigsnarf.wordpress.com/2013/02/20/classifying-malicious-dns-with-22-features-using-random-forests-presentation/
I should also note that there are “DNS Firewalls” that inspect traffic and also work on blacklists to block. I also saw a DNSsec course.